Introduction to PingOne Protect
PingOne Protect is a cloud-based service that applies machine learning and configurable, intelligent security policies to analyze user identity and detect potential threats.
PingOne Protect combines multiple internal and external risk factors to provide a single access point for calculating and retrieving risk scores. Use the user interface to create risk policies and configure the scores of various risk predictors into a single risk score. You can also view data and analytics on high-risk events and get in-depth insights on the authentication behavior of your users.
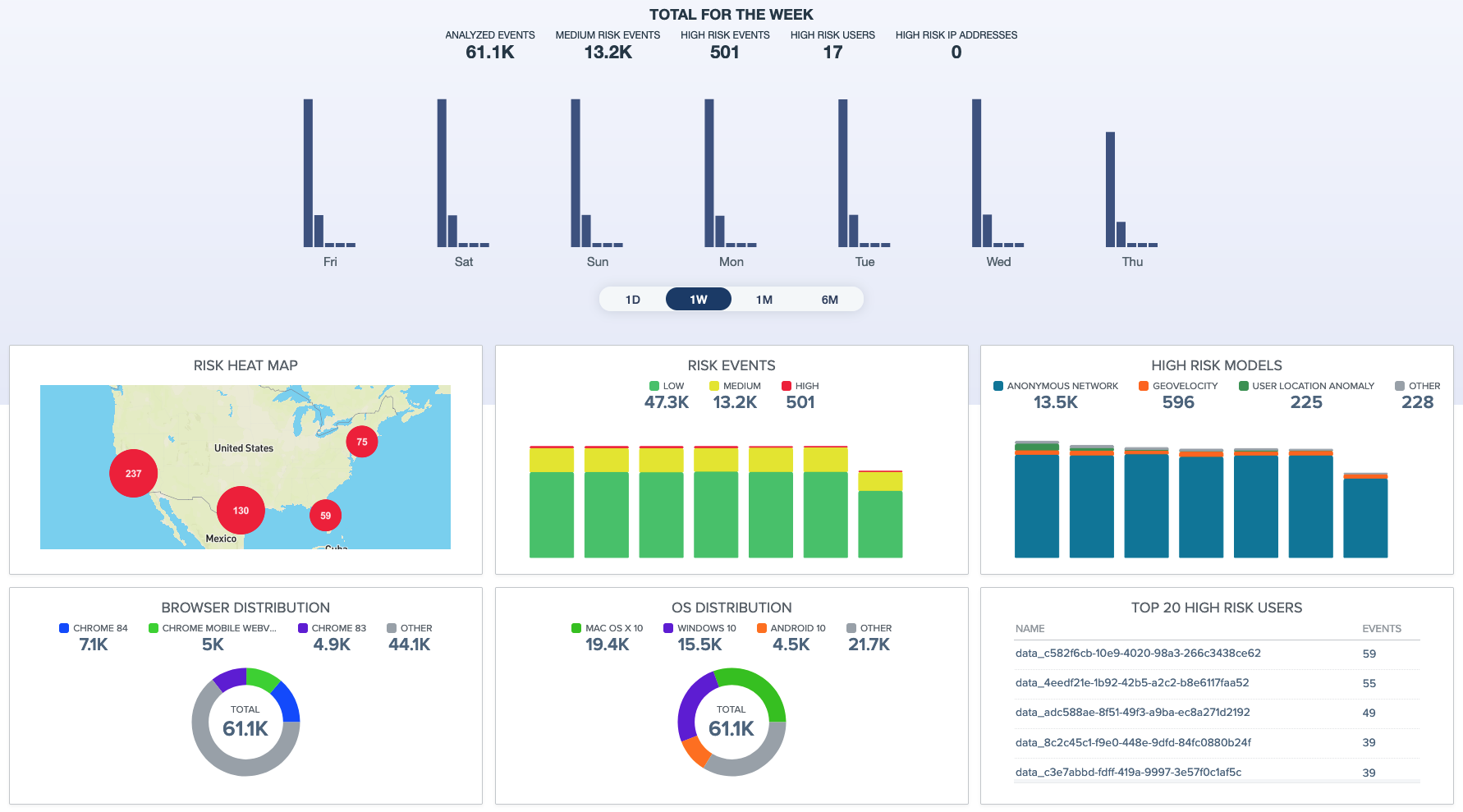
By implementing risk policies, you can control the authentication flow depending on the risk level. For example, you can force high-risk users to step up to stronger authentication or deny them access while providing a frictionless experience for trusted users.
PingOne Protect leverages the following predictors to learn user behavior and detect anomalies:
-
Adversary-in-the-Middle
-
Anonymous network detection
-
Bot detection
-
Device (new device and suspicious device)
-
Email reputation
-
Geovelocity anomaly
-
IP reputation
-
PingID device trust
-
Traffic anomaly
-
User-based risk behavior
-
User location anomaly
-
Velocity (user velocity and IP velocity)
|
The suspicious device and bot detection predictors are only available if you have a license for PingOne Protect. If you have a PingOne Risk license, contact your account team for more details. |
Learn more in PingOne Protect key concepts and the PingOne Protect Datasheet.