Connecting an HTTP service
Configure HTTP settings to connect PingOne Authorize to an HTTP service.
Before you connect to an HTTP service, you can add attributes that store values for service settings, such as the endpoint URL for an HTTP request. Storing settings as attributes is useful if the values are dynamic, or if you want to use different values during testing. For example, during testing, you can override a production REST API used in an HTTP service with a test API.
|
If the service requires OAuth 2.0 Client Credentials authentication, you must add an attribute that stores the external service’s client secret before you configure service settings. You can also add attributes that store other client credentials, such as the client ID and token endpoint. |
After you finish configuring the service, test the service connection. To make the service response available in policies, add attributes that resolve against the service and process the response to extract required values.
Add a service, configure the following service settings, and then configure general settings to finish the service connection.
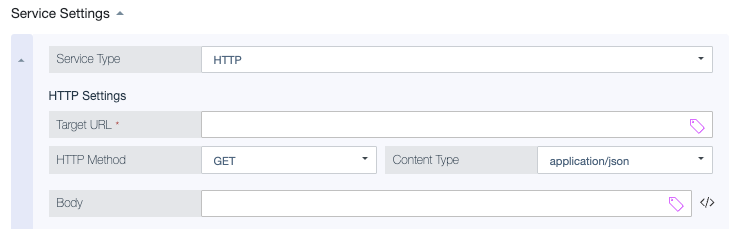
HTTP Settings
HTTP service requests can send and receive text, JSON, and XML content.
| Setting | Description | ||
|---|---|---|---|
Target URL |
The URL for the REST endpoint that the decision point accesses in the HTTP request. To include an attribute anywhere in the URL, wrap the full name of the attribute in double curly brackets.
|
||
HTTP Method |
The action performed in the HTTP request. Options are GET, POST, PUT, DELETE, and HEAD. |
||
Content Type |
The media type of the content in the HTTP request. Options are application/json, application/xml, text/html, and text. |
||
Body |
The body to send with the HTTP request. You can include attributes anywhere in the body, with no escaping, by wrapping the full name of the attribute in double curly brackets.
|
Headers
You can send any number of custom header key-value pairs with a request. To make the header dynamic, select an attribute for the header value.
To improve cache performance, you can also define headers to exclude from the service cache key. Learn more in Service caching.
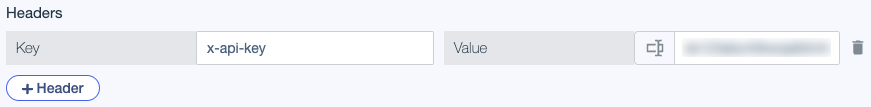
To add a header:
-
Click Header.
-
Enter the header Key.
The key is a fixed string.
-
For the header Value, enter a constant value or click
 to select an attribute.
to select an attribute.
SSL/TLS Certificate Settings
Certificate validation in PingOne Authorize allows you to enable or disable SSL and TLS certificates when connecting to SSL or TLS-based services.
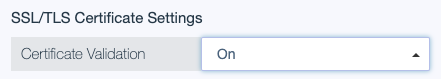
SSL and TLS certificate settings apply when validating the certificate or certificate chain sent from the server. The following Certificate Validation options are available:
-
On: Performs TLS validation when connecting to the service. Select this option when you connect to a service that has a certificate issued from a valid certificate authority. This setting is enabled by default.
-
Off: Skips server certificate validation and allows initiation of the connection without validation.
HTTP authentication methods
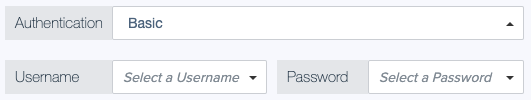
By default, no authentication method is selected for HTTP service requests. To authenticate such requests, you can use basic authentication with a username and password, a bearer token, or the OAuth 2.0 Client Credentials flow.
None
With this method, no authorization header is sent with the HTTP request. This is the default option.
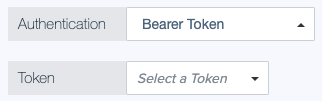
Bearer Token
For bearer authentication with a static token, select an attribute that stores the authorization token to send with the HTTP request.
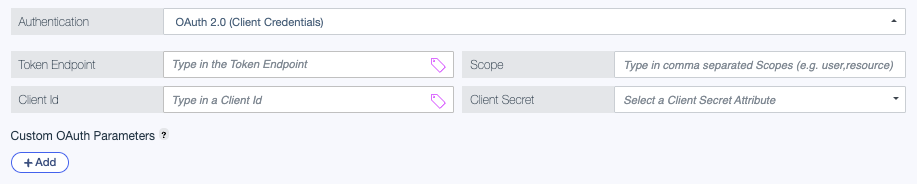
OAuth 2.0 (Client Credentials)
For authentication with the OAuth 2.0 Client Credentials flow, configure client credentials to exchange for an access token.
PingOne Authorize manages the authentication process as follows:
-
PingOne Authorize requests an access token for the external service by sending client credentials, including any scopes, in a POST request to the authorization server’s token endpoint.
PingOne Authorize always sends client credentials in the HTTP request body (
client_secret_post) and doesn’t support using theAuthorizationheader (client_secret_basic).If you’re using an HTTP service to access PingOne APIs, configure your PingOne worker application to use
client_secret_postto ensure that client credentials are sent in the body of the token request, as expected by the service.If the worker application is configured to use
client_secret_basic, requests for access tokens from PingOne Authorize will fail with an authentication error. -
The authorization server validates the client credentials and provides an access token, which PingOne Authorize caches. When the external service no longer accepts this token, PingOne Authorize reuses the client credentials to get a new one.
-
In an HTTP service request, PingOne Authorize provides the access token in the
Authorizationheader, authenticates with the HTTP service, and retrieves the requested information from the service.
Before you configure the following settings, add an attribute that stores the client secret. You can also add attributes that store other client credentials.
-
Token Endpoint: The token endpoint URL for the authorization server that grants an access token. For example,
https://{domain}/oauth*/token. -
Scope (optional): The scopes to request in the access token. Scopes are optional and can be used to limit the permissions of a token in the connected service. Separate scopes with commas and no spaces.
-
Client Id: Enter the external service’s unique client identifier, or select an attribute that stores this value.
-
Client Secret: Select an attribute that stores the external service’s client secret.
-
Custom OAuth Parameters (optional): A list of custom key-value pairs representing additional parameters sent in the body of the token endpoint request. This level of customization is useful when integrating with authorization servers that enforce specific configuration constraints.
The Key must be a fixed string. For the Value, enter a constant value or click
 to select an attribute.
to select an attribute.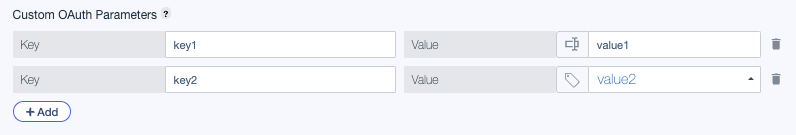
Custom OAuth parameters have the following constraints:
-
You can define up to 10 key-value pairs.
-
Keys cannot contain spaces in any position.
-
Keys must be between 1 - 128 characters in length.
-
You cannot use any of the following values as a key (case-sensitive):
-
client_id -
client_secret -
scope -
grant_type
-
-
Value processors
You can define value processors to transform data returned by the HTTP service. Learn more in Processors.