Creating an outbound provisioning rule for a connection through an LDAP gateway (early access)
Create a rule to define which users are provisioned and how attributes are mapped between PingOne and the LDAP directory.
Before you begin
Make sure you have:
-
Created an LDAP gateway connection.
The connection must be enabled before you can use it in a rule. Learn more in Connections.
Not all provisioning connection types support inbound provisioning. Learn more in Provisioning.
-
The RDN attribute that specifies the relative portion of the DN (distinguished name), which uniquely identifies the user in the LDAP directory.
-
The directory path (LDAP base DN) that specifies the LDAP directory location from where users and groups are synced into PingOne.
Steps
-
In the PingOne admin console, go to Integrations > Provisioning.
-
Click and then click New Rule.
-
For Sync Direction, select PingOne as Source.
-
For Available Connections, click next to the appropriate LDAP gateway connection to set it as the target and then click Continue.
-
In the Rule Details panel, enter a name and description for the rule and then click Next.
-
In the Directory Configuration panel, set directory settings for users and groups.
-
In the Directory Path (LDAP Base DN) field, enter the LDAP base DN that specifies the LDAP directory location from where users and groups are synced into PingOne. Learn more in Distinguished Names in the Microsoft LDAP documentation.
-
In the RDN Attribute field, select the PingOne attribute that will map to the RDN attribute. The RDN attribute is the relative portion of the DN (distinguished name) that uniquely identifies the user in the LDAP directory
The default attributes are based on the directory type of the gateway used.
-
For Active Directory,
RDNdefaults tocn. -
For PingDirectory,
RDNdefaults touid.
-
-
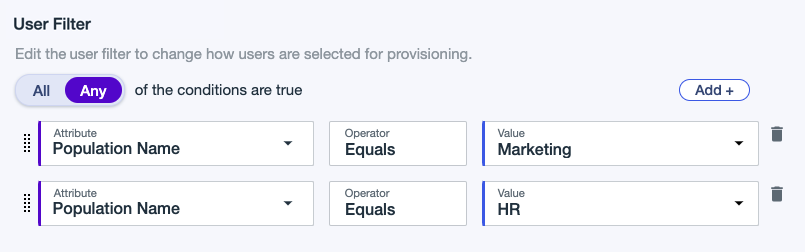
For User Filter, click Add + to enter a user filter and define which users to include in provisioning based on population or user attributes. Learn more in Example user filters.
-
Enter the first condition:
-
Select All or Any to determine how the linked conditions will be evaluated: Boolean logical AND or OR.
-
Attribute: The user attribute to filter on.
-
Operator: Equals is the only operator supported at this time.
-
Value: Enter the appropriate value.
If you select a group in the filter, updating or deleting the group can cause the provisioning rule to resync.
If you select a group in the filter, the filter will include all users with any kind of membership in the group. Learn more in Groups.
-
-
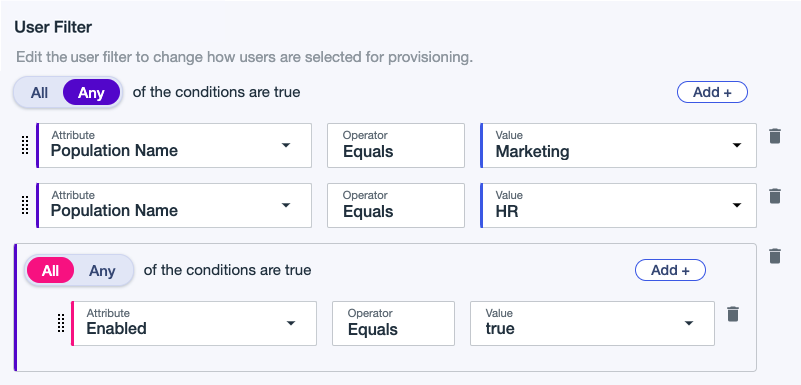
(Optional) Click Add + to add another condition or condition set.
-
To delete a condition, click the Delete icon.
Group provisioning isn’t available.
-
-
-
Click Next.
-
In the Attribute Mapping panel, map attributes between the source and PingOne to ensure users are provisioned correctly.
The default attributes are based on the directory type of the gateway used. For outbound provisioning, the RDN attribute defaults to cn for Active Directory.
-
To add an attribute mapping, click Add and enter the source and target attributes.
-
To use the expression builder, click the Gear icon. Learn more in Using the expression builder. You can also use list values in the expression builder to create advanced expressions, such as conditional statements.
-
Select values from the Expression list. Some attributes have metadata that define potential values.
For example, for Salesforce attribute mapping, you can see a list of values from Salesforce in the form of an Expression list. In the expression builder, enter a single quote to see potential values.
You can use a switch statement or an if-else statement to evaluate an expression based on a pattern match.
For example, to match an
accountIdattribute, enter the following in the expression builder:#core.switchExpr(#root.accountId, '0000EXAMPLEID', 'Valid' , 'Invalid')
For a switch statement with multiple cases and a match, enter the following in the expression builder:
#core.switchExpr(#root.accountId, '0000EXAMPLEID1', 'Full Access', '0000EXAMPLEID2', 'Restricted Access' , '0000EXAMPLEID3', 'Read-only Access', 'No Access')
The email attribute mapping is checked by default and included in updates.
-
-
To delete a mapping, click the Delete icon.
-
-
Click Save.
-
To enable the rule, click the toggle at the top of the details panel to the right (blue).
You can disable the rule by clicking the toggle to the left (gray).
Result
The Sync Status appears and the rule is listed under Rules. Learn more about Sync status.
Example user filters early access
This section shows some example user filters to define users for provisioning.
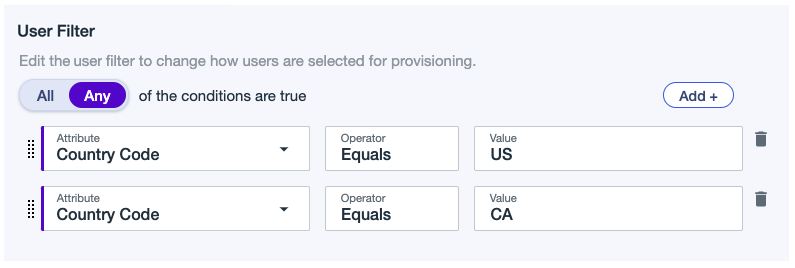
Example 1
A filter that includes users from the USA and Canada. Include users that match the following:
Country Code Equals US
OR
Country Code Equals CA
Example 2
A filter that includes users from the following populations:
Population Name Equals Marketing
OR
Population Name Equals HR