Enable Device Management node
The Enable Device Management node controls the restrictions placed on users who want to reset or remove registered multi-factor authentication (MFA) devices.
By default, authenticated users can only remove a registered MFA device if they have authenticated by using a matching device. For example, to delete a device registered for OATH, they must have successfully authenticated by using a journey that includes an OATH Token Verifier node.
You can use this node in a journey to relax or remove this restriction.
Compatibility
| Product | Compatible? |
|---|---|
Advanced Identity Cloud |
Yes |
PingAM (self-managed) |
Yes |
Ping Identity Platform (self-managed) |
Yes |
Inputs
The node requires that the username of the identity authenticating is acquired previously in the journey. For example, by using a
Platform Username node.
Configuration
| Property | Usage | ||
|---|---|---|---|
Device Check Enforcement Strategy |
The MFA authentication method that is required to allow users to remove registered devices. Choose from:
The default is |
Outputs
This node adds a flag to the auth session the journey creates, depending on the Device Check Enforcement Strategy property.
The flag determines which MFA device types, if any, the user can delete.
Outcomes
Success-
Any of the following situations result in the Success outcome from this node:
-
The Device Check Enforcement Strategy is set to
SAME.This setting relies on existing behavior to update the auth session and makes no changes of its own.
-
The Device Check Enforcement Strategy is set to
ANY, and at least one MFA type was used previously in the journey. -
The Device Check Enforcement Strategy is set to
NONE, and the node was able to update the auth session.
-
Failure-
Any of the following situations result in the Failure outcome from this node:
-
The
usernameproperty of the identity is not available. -
The user is marked as inactive.
-
The Device Check Enforcement Strategy is set to
ANY, but the authentication journey didn’t perform MFA. -
The node attempted to update the auth session but did not succeed.
-
Example
The following example journey allows users to reset their registered MFA devices without having to authenticate using MFA.
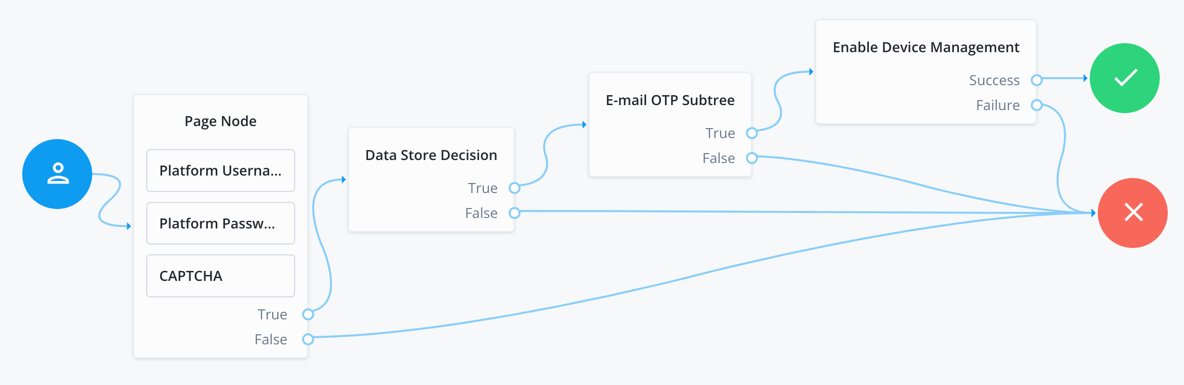
-
The user enters their credentials, completes the CAPTCHA, and is verified against the identity store.
-
A subtree sends a one-time passcode (OTP) to the user’s email address to verify they have access to the address they have in their profile.
-
The Enable Device Management node, with the Device Check Enforcement Strategy property set to
NONE, upgrades the session the user receives to allow them to delete any of their registered MFA devices.