ESVs
Environment secrets and variables (ESVs) let you individually configure your sandbox[1], development, UAT[2], staging, and production tenant environments in PingOne Advanced Identity Cloud.
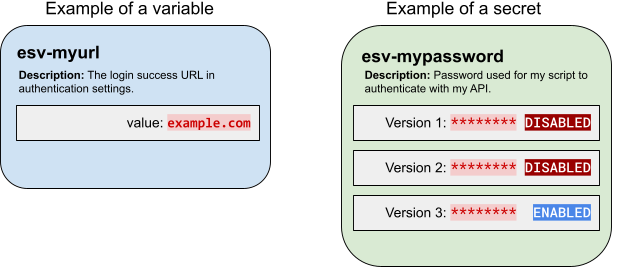
Use variables to set values that need to be different for each tenant environment. For example, an authentication node might need one URL in your development environment, but a different URL in your production environment.
Use secrets to set values that need encrypting. The values may or may not need to be different for each tenant environment. For example, an MFA push notification node might need an authorization password to use an external SMS service.
| ESV data is held in a global service and not subject to regional data storage. You therefore must not store personally identifiable information (PII) in ESVs. You are responsible for ensuring that your use of ESVs complies with all applicable data protection laws and regulations. |
| ESVs are an Advanced Identity Cloud only feature. In particular, ESV secrets should not be confused with secrets in the self-managed PingAM or PingIDM products. |
Variables
Use ESV variables to set configuration values that need to be different for each tenant environment.
Variables are simple key-value pairs. Unlike secrets, they are not versioned. They should not contain sensitive values. The value of a variable must not exceed a maximum length of 65535 bytes (just under 64KiB).
You can reference ESV variables from configuration placeholders or scripts after you:
-
Create or update the variables using the variables APIs or the Advanced Identity Cloud admin console.
-
Restart Advanced Identity Cloud services using the restart API or by applying updates in the Advanced Identity Cloud admin console.
Other ways of restarting Advanced Identity Cloud services, such as by running a promotion, won’t load ESV changes. This makes it easier to identify issues caused by ESV changes.
The following table shows how to reference an ESV variable with the name esv-my-variable:
| Context | How to reference | Access as soon as set |
|---|---|---|
Configuration placeholders |
|
|
Scripts |
|
|
Variable expression types
You must use the expressionType parameter to set an expression type when you create an ESV variable. This
lets Advanced Identity Cloud correctly transform the value of the ESV variable to match the configuration property expression type
when substituting it into configuration.
The expression type is set when the ESV variable is created, and it cannot be modified.
Before the expressionType parameter was introduced, it was only possible to set expression types from
within configuration, using expression level syntax; for example, {"$int": "&{esv.journey.ldap.port|1389}"}.
The expressionType parameter supplements this expression level syntax and allows the ESV type
to be identified without inspecting configuration.
Make sure the expression type that you set in configuration matches the expression type that you set in the ESV expressionType parameter.
|
| Expression type | Description | Examples | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
String value (default) |
|
||||||||||||
|
JSON array |
|
||||||||||||
|
JSON object |
|
||||||||||||
|
Boolean value |
|
||||||||||||
|
Integer value |
|
||||||||||||
|
This type can transform any number value (integers, doubles, longs, and floats). |
|||||||||||||
|
Comma-separated list |
|
Existing ESVs will be migrated to use the expressionType parameter. If any existing ESVs contain
combined types, they will be split into separate ESVs by the migration process.
|
Secrets
Use ESV secrets to set configuration values that need encrypting. The values may or may not need to be different for each tenant environment.
You can reference ESV secrets from configuration placeholders or scripts after you:
-
Create or update the secrets using the secrets APIs or the Advanced Identity Cloud admin console.
-
Restart Advanced Identity Cloud services using the restart API or by applying updates in the Advanced Identity Cloud admin console.
Other ways of restarting Advanced Identity Cloud services, such as by running a promotion, won’t load ESV changes. This makes it easier to identify issues caused by ESV changes.
You can reference secrets that are signing and encryption keys by mapping them to secret labels. Secrets referenced by secret label mappings can be accessed as soon as the ESV is set; restarting Advanced Identity Cloud services is not required.
The following table shows how to reference an ESV secret with the name esv-my-secret:
| Context | How to reference | Access as soon as set |
|---|---|---|
Configuration placeholders |
|
|
Scripts |
|
|
Signing and encryption keys |
Secret versions
Instead of having a single value, ESV secrets have one or more secret versions, each containing their own value. By design, the value of a secret version cannot be read back after it has been created. The value of a secret version must not exceed a maximum length of 65535 bytes (just under 64KiB).
To create a new secret version, its value must be different from the value of the latest secret version. If you try to create a new secret version with the same value as the latest version, the existing version is retained and no changes are made.
You can enable or disable secret versions by setting their status field to ENABLED or DISABLED using the REST API or clicking the Active toggle in the admin console.
The latest version of a secret must be enabled for it to be used in your configuration.
The following rules ensure that a secret always has at least one enabled version:
-
When you create a secret, the first version of the secret is automatically created and is enabled.
-
You cannot disable the latest version of a secret.
-
You cannot delete the latest version of a secret if the previous version is disabled.
| Secret versions are an important feature of key rotation. Learn more in Rotate keys in mapped ESV secrets. |
Encoding format
You can use the encoding parameter to set an encoding format when you create an ESV secret:
| Encoding format | Description |
|---|---|
|
Use this format for secrets that are not keys, such as passwords. |
|
Use this format for asymmetric keys; for example, a public and private RSA key pair. Learn more in Generate an RSA key pair. |
|
Use this format for AES keys; for example, an AES-256 key. Learn more in Generate an AES or HMAC key. |
|
Use this format for HMAC keys; for example, a HMAC-SHA-512 key. Learn more in Generate an AES or HMAC key. |
Control access to secrets
There are 3 contexts where you can access an ESV secret:
-
From configuration placeholders; learn more in Configure placeholders to use with ESVs.
-
From scripts; learn more in Use ESVs in scripts.
-
From mapped secret labels (for signing and encryption keys); learn more in Use ESVs for signing and encryption keys.
However, if the secret contains a signing and encryption key, you may want to restrict access from
configuration placeholder and script contexts. To do this, you can use the useInPlaceholders
boolean parameter when you create the secret:
| Context | Unrestricted access | Restricted access |
|---|---|---|
|
|
|
Configuration placeholders |
|
|
Scripts |
|
|
Mapped secret labels |
|
|
| You can only set restricted access using the API. The UI currently creates secrets only with unrestricted access. |
Preconditions to delete an ESV
Before you delete an ESV, you may need to remove references to it from your environment:
-
You cannot delete an ESV if it is referenced in a configuration placeholder. You must first remove the placeholder from configuration. Learn more in Delete an ESV referenced by a configuration placeholder.
-
You cannot delete an ESV if it is referenced in a script. You must first remove any scripts that reference the ESV.
-
You cannot delete an ESV if it is referenced in an orphaned script[3]. You must first remove any orphaned scripts. You can do this by running a self-service promotion (which automatically cleans up orphaned scripts).
ESV naming
ESV API naming convention
The names of secrets and variables need to be prefixed with esv- and can only contain
alphanumeric characters, hyphens, and underscores; for example, esv-mysecret-1 or
esv-myvariable_1. The maximum length, including prefix, is 124 characters.
ESV legacy naming convention and API compatibility
Before the introduction of the ESV API endpoints, if ESVs were defined on your behalf as part of
the promotion process, they were prefixed with byos-. Advanced Identity Cloud uses compatibility behavior to
let you still use these legacy ESVs. The compatibility behavior depends on how far the legacy ESVs
were promoted through your development, staging, and production tenant environments:
- Development, staging, and production environments
-
If you promoted a legacy ESV to all your tenant environments, it will have been duplicated during the ESV migration process, so will be available in the API using the new
esv-prefix.For example,
byos-myvariable123will appear asesv-myvariable123. Scripts that reference the legacy ESV will still work; bothbyos-myvariable123andesv-myvariable123resolve to the same ESV. - Development and staging environments only
-
If you never promoted a legacy ESV to your production environment, it will have been ignored during the ESV migration process. However, you can still use the ESV API to create it in your production environment, as the compatibility behaviour looks for new ESVs that have a naming format like a legacy ESV (
byos-<hash>-<name>). So any ESVs that are created with a naming format ofesv-<hash>-<name>will also automatically create abyos-<hash>-<name>duplicate.For example, creating a new ESV called
esv-7765622105-myvariablewill automatically create another ESV calledbyos-7765622105-myvariable. Scripts that reference the legacy ESV will still work; bothbyos-7765622105-myvariableandesv-7765622105-myvariableresolve to the same ESV.