Google Chrome Device Trust node
Use the Google Chrome Device Trust node to establish device trust with Chrome Enterprise.
Compatibility
| Product | Compatible? |
|---|---|
Advanced Identity Cloud |
Yes |
PingAM (self-managed) |
Yes |
Ping Identity Platform (self-managed) |
Yes |
Inputs
This node reads the challengeresponse property from the journey state.
This property is populated by a Scripted Decision node that retrieves the
value from PingGateway.
Dependencies
This node requires:
Set up PingGateway
-
Install PingGateway as indicated in the Quick Install Guide.
-
Configure the
admin.jsonfile to run PingGateway on ports 9090 / 9443. Learn more about starting up PingGateway with custom settings.If 9443 is for HTTPS, then readers need to configure PingGateway for server-side HTTPS. Learn more in Configure PingGateway for TLS.
-
Download the generate_challenge.json and challengeresponse.json JSON route files.
-
Store the two JSON route files in your
routesdirectory, for example:-
$HOME/.openig/config/routes (on Mac or Linx) or
-
%appdata%\OpenIG\config\routes (on Windows).
-
-
Download and store the getChallenge.groovy Groovy script file in your
groovydirectory, for example:-
$HOME/.openig/scripts/groovy (on Mac or Linux), or
-
%appdata%\OpenIG\scripts\groovy (on Windows).
If you do not have the
groovydirectory, create one.
-
About PingGateway routes
The generate_challenge.json route executes the getChallenge.groovy Groovy
script to perform the following tasks:
-
Make an
HTTP POSTrequest to the Google Chrome Verified Access API to generate the challenge. -
Get the challenge from the API response.
-
Set the challenge as the value of the x-verified-access-challenge custom HTTP response header.
Google Chrome recognizes the custom HTTP response header and uses the challenge value to calculate a challenge-response.
-
Finally, Google Chrome creates a new custom HTTP request header, x-verified-access-challenge, and sets the challenge-response as the header value.
The generate_challenge.json route redirects the user to the challengeresponse.json route to perform these tasks:
-
Get the challenge-response from the request headers.
-
Set the challenge-response value in the query parameter of the redirect URL as the
challengeresponsekey. -
Redirect back to Advanced Identity Cloud.
Set up Scripted Decision node
This node requires a
Scripted Decision node earlier in the
journey to redirect the end user to PingGateway to generate and retrieve the
challengeresponse.
-
Configure a Script Decision node. The following is an example script used in the Script Decision node.
Example Script Decision Node redirect script.
try { var redirectMethod = "GET"; var redirectUrl = "https://ig.example.com:9443/pinggateway-route-name"; if (!requestParameters.get("challengeresponse")) { callbacksBuilder.redirectCallback(redirectUrl, {}, redirectMethod, true); } else { var challenge = requestParameters.get("challengeresponse"); nodeState.putShared("x-verified-access-challenge", challenge); action.goTo("true"); } } catch (error) { nodeState.putShared("errorMessage", error.toString()); action.goTo('false').withErrorMessage(error); }-
The above script uses the Next Generation Script Engine.
-
The
challengeresponseparameter must be in the redirect to Advanced Identity Cloud as a query parameter from PingGateway. -
The Google Chrome Device Trust node retrieves the
challengeresponsevalue from the request parameters.
-
Configuration
| Property | Usage |
|---|---|
API Key |
The Google Cloud API key. |
Private Key |
Google Cloud administrator credential’s private key. |
Key ID |
The credential used to verify the authenticity and integrity of the JWT. |
Credentials Client Email |
The email ID of the client with Google Cloud administrator credentials. |
Outcomes
Continue-
Successfully authenticated the user.
Error-
The journey follows this outcome path if the node is unable to obtain the device trust signals.
Troubleshooting
If this node logged an error, review the log messages for the transaction to find the reason for the exception. Review the GCP configuration for the Chrome Enterprise Device Trust node and contact Google Support for further information.
Example
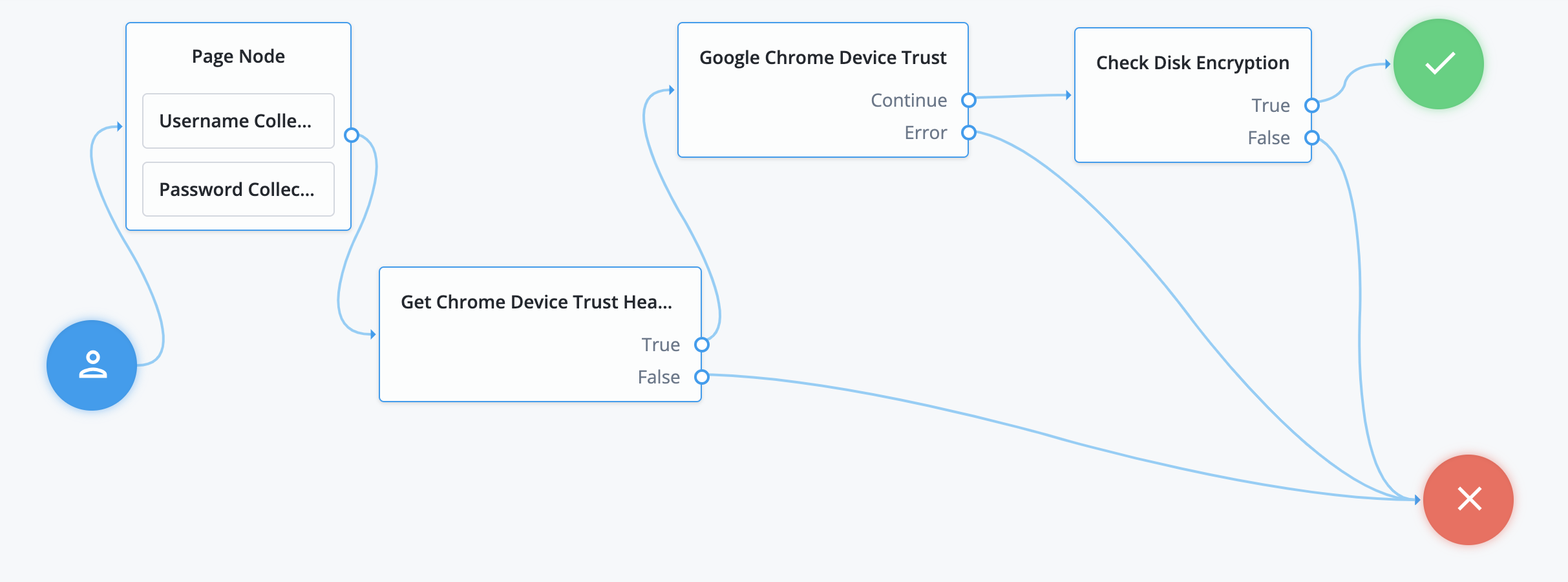
The example journey shows the following:
-
A user logs in.
-
The Chrome Device Trust Headers node, a Scripted Decision node, redirects to PingGateway to handle the Google Chrome challenge-response process.
-
PingGateway generates the challenge, retrieves the challenge response, and sets it as a request parameter before redirecting back to the journey.
-
The Google Chrome Device Trust node uses the challenge response to retrieve Chrome Device Trust signals, storing them in transient state.
-
The Check Disk Encryption node, another Scripted Decision node, determines if the
diskEncryptionsignal is disabled or enabled and makes an informed access decision.The sample script used in this node.
var diskEncrypted = nodeState.get("deviceSignals").get("diskEncryption"); if(diskEncrypted === "DISK_ENCRYPTION_DISABLED") { outcome = "true" } else { outcome = "false" }