Configure federated access for tenant administrators
Federated access lets tenant administrators use your company’s single sign-on (SSO) to sign on to your PingOne Advanced Identity Cloud tenant environments.
By using federation to authenticate your tenant administrators to Advanced Identity Cloud, you can quickly and easily provision and deprovision users from your centralized identity provider (IdP) instead of managing them separately in each Advanced Identity Cloud tenant environment.
The groups feature allows you to add and remove tenant administrators depending on their group membership in your IdP. You can also specify the level of administrator access (super administrator[1] or tenant administrator) for groups of users.
Advanced Identity Cloud lets you configure federated access in two main ways:
-
You can use PingOne to configure PingOne itself as an IdP for Advanced Identity Cloud. Learn more in Configure federated access using PingOne.
-
You can use the Advanced Identity Cloud admin console to configure Microsoft Entra ID (Entra ID)[2] or Microsoft Active Directory Federation Services (AD FS) as IdPs, or any other IdP that’s OpenID Connect (OIDC) compliant. Learn more in Configure federated access using PingOne Advanced Identity Cloud.
Configure federated access using PingOne
You can configure PingOne as a federation IdP for PingOne Advanced Identity Cloud. To do this, configure it in PingOne itself. Learn more in Set up SSO to PingOne Advanced Identity Cloud.
After you configure PingOne as a federation IdP, each configured tenant environment in Advanced Identity Cloud automatically displays PingOne in its list of federation IdPs:
-
Sign on to the Advanced Identity Cloud admin console for any of the environments you configured for federated access using PingOne.
-
Go to Tenant settings.
-
Click Federation.
-
If configured correctly in PingOne, the list contains an active PingOne federation IdP:
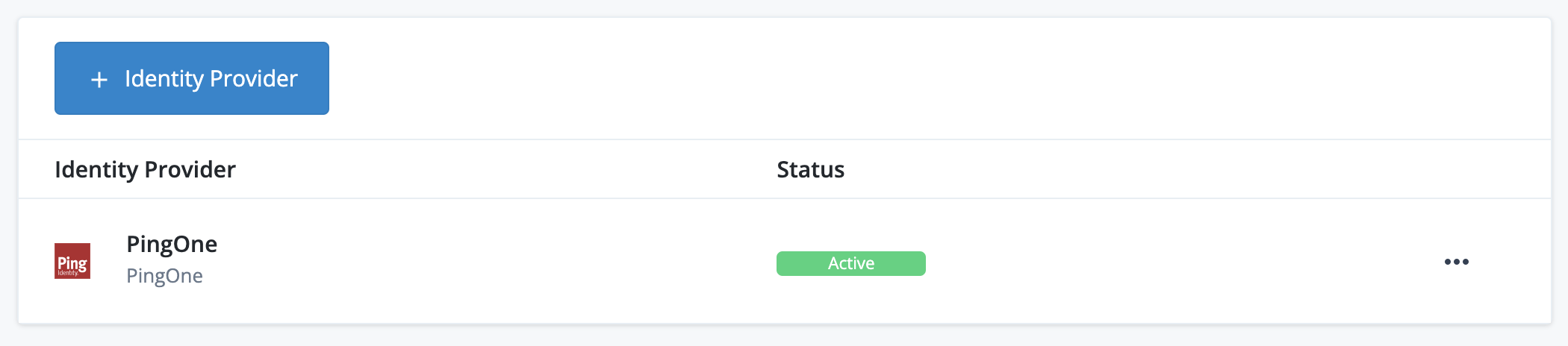
-
Click the PingOne list item to view its configuration settings page. For PingOne, this is a basic page containing the Status and the Well-Known Endpoint of the PingOne federation IdP:
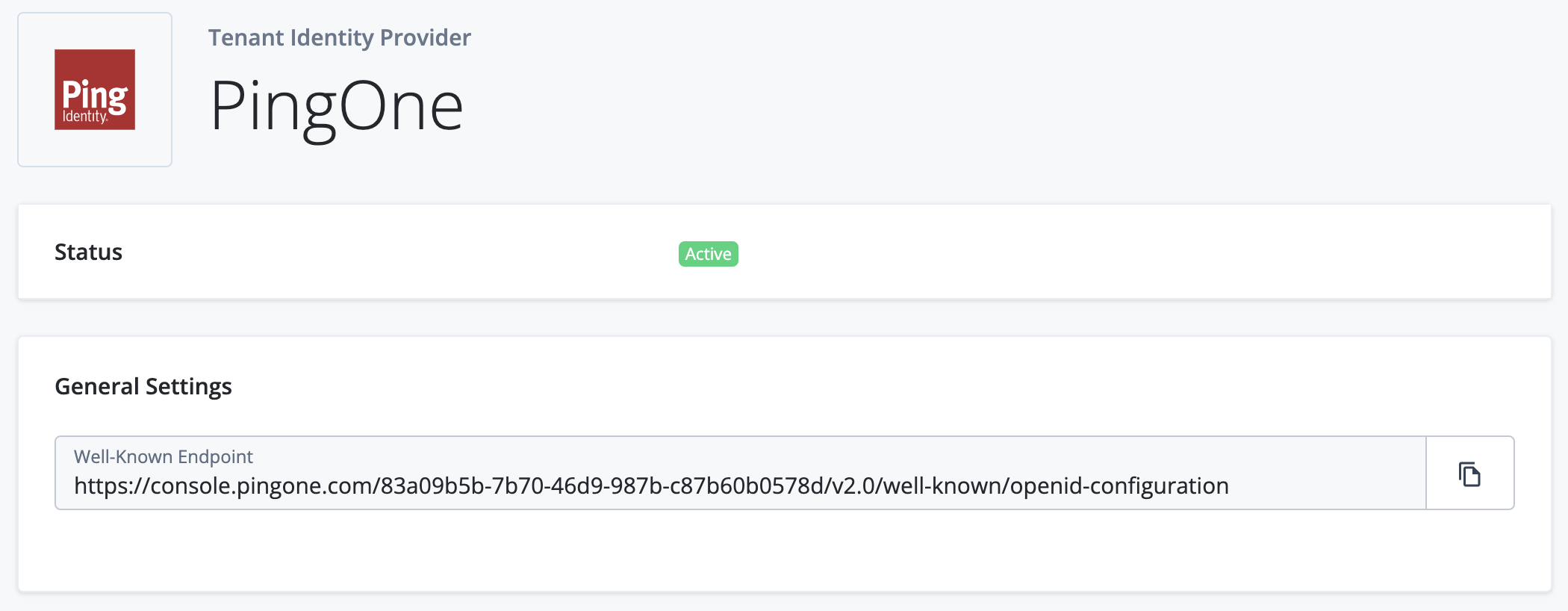
If you configure a federation IdP in PingOne, the corresponding Advanced Identity Cloud tenant environments are configured automatically. You do not need to promote configuration changes.
Configure federated access using PingOne Advanced Identity Cloud
You can configure the following federation IdPs using the Advanced Identity Cloud admin console:
If you configure a federation IdP using the Advanced Identity Cloud admin console, you must do so in your development environment and promote the configuration changes. You must also store the federation IdP secrets for each of your environments in ESV secrets and set corresponding placeholders in your configuration. Learn more in Configure federated access across your tenant environments.
Configure federated access across your tenant environments
The high-level process to set up federated access across your tenant environments is as follows:
-
Set up a federation IdP for your development environment:
-
You can use the same federation IdP for all your tenant environments, or you can use a different federation IdP for each environment.
-
If you use the same federation IdP for multiple environments, you must configure it with redirect URLs for each environment. The redirect URL for a tenant environment has the following format:
https://<tenant-env-fqdn>/login/admin
-
Note the client secret of the IdP, as you might not be able to retrieve it later.
-
-
In your development environment:
-
Create the following ESVs using the values from the federation IdP configuration:
You can create variables and secrets using the Advanced Identity Cloud admin console or the API.
-
Create a variable or create a secret using the Advanced Identity Cloud admin console.
-
Create a variable or create a secret using the API.
-
Federation IdP fields:
ESV name ESV type Expression type Example value esv-idp-client-idVariable
String
6b05a314-c721-4aa6-baad-7f533cbd25b0
esv-idp-client-secretSecret
String
changeit
esv-idp-user-info-endpoint[3]Variable
String
https://graph.microsoft.com/oidc/userinfo
-
Federation IdP endpoint fields (choose one of the following):
-
Option 1: Create a single ESV containing the well-known endpoint ID:
ESV name ESV type Expression type Example value esv-idp-well-known-endpoint-idVariable
String
0e076864-135f-4914-9b72-80efaa4c3dcf
-
Option 2: Create an ESV for each of these endpoint fields:
ESV name ESV type Expression type Example value esv-idp-well-known-endpointVariable
String
https://login.microsoftonline.com/0e076864-135f-4914-9b72-80efaa4c3dcf/v2.0/.well-known/openid-configuration
esv-idp-authorization-endpointVariable
String
https://login.microsoftonline.com/0e076864-135f-4914-9b72-80efaa4c3dcf/oauth2/v2.0/authorize
esv-idp-token-endpointVariable
String
https://login.microsoftonline.com/0e076864-135f-4914-9b72-80efaa4c3dcf/oauth2/v2.0/token
esv-idp-issuerVariable
String
https://login.microsoftonline.com/0e076753-135f-4914-9b72-80efaa4c3dcf/v2.0
You don’t need to create an ESV for the redirect URL, as Advanced Identity Cloud automatically configures it based on the environment’s FQDN. -
-
(Optional) Federation IdP groups fields:
ESV name ESV type Expression type Example value esv-idp-super-admins-groupVariable
String
8c578f67-cac4-49eb-8f28-8e4f2c22945e
esv-idp-tenant-admins-groupVariable
String
3623050d-3604-45a2-942e-f6be9ec9f9ed
esv-idp-tenant-auditors-groupVariable
String
eeb11282-cb38-42b9-909f-439cad25550e
-
-
Follow the instructions in Configure a mutable environment to use a federation IdP, entering the following ESV placeholders in the relevant fields:
-
Federation IdP fields:
Field name ESV placeholder Application ID
&{esv.idp.client.id}Application secret
&{esv.idp.client.secret}User Info endpoint[3]
&{esv.idp.user.info.endpoint} -
Federation IdP endpoint fields (choose one of the following):
-
Option 1: If you created a single ESV for the well-known endpoint ID, replace the ID portion of the endpoint’s value with the ESV placeholder. Use the following examples as guidance:
Field name Example using ESV placeholder Well-known endpoint
https://login.microsoftonline.com/
&{esv.idp.well.known.endpoint.id}/v2.0/.well-known/openid-configurationAuthorization endpoint
https://login.microsoftonline.com/
&{esv.idp.well.known.endpoint.id}/oauth2/v2.0/authorizeToken endpoint
https://login.microsoftonline.com/
&{esv.idp.well.known.endpoint.id}/oauth2/v2.0/tokenIssuer
https://login.microsoftonline.com/
&{esv.idp.well.known.endpoint.id}/v2.0 -
Option 2: If you created an ESV for each endpoint, insert the ESV placeholders into their respective endpoint fields:
Field name ESV placeholder Well-known endpoint
&{esv.idp.well.known.endpoint}Authorization endpoint
&{esv.idp.authorization.endpoint}Token endpoint
&{esv.idp.token.endpoint}Issuer
&{esv.idp.issuer}
-
-
(Optional) Federation IdP groups fields:
Field name ESV placeholder Group Identifiers field to the left of Super Admins
&{esv.idp.group.super.administrators}Group Identifiers field to the left of Tenant Admins
&{esv.idp.group.tenant.administrators}Group Identifiers field to the left of Tenant Auditor
&{esv.idp.group.tenant.auditors}
-
-
-
Determine the promotion order of your tenant environments. This will depend on whether you have a standard promotion group of environments or whether you also have additional UAT environments.
-
In promotion order, for each of the tenant environments in your promotion group, perform the following steps:
-
Repeat step 1 to create a federation IdP for the tenant environment.
-
Repeat step 2a to create the same ESVs in the tenant environment. Ensure the ESV values match those from the tenant environment’s federation IdP configuration.
-
Run a promotion to move the configuration changes to the tenant environment from its respective lower tenant environment. Learn more in:
-
-
(Optional) If you have sandbox[4] environments, repeat steps 1 and 2 for each sandbox environment.
Set up a federation IdP
You can find instructions for setting up a federation IdP in the following guides:
Configure a mutable environment to use a federation IdP
After you’ve set up a federation IdP, you can configure it in a mutable environment (development or sandbox[4]) to provide federated access to tenant administrators.
| To understand how the instructions in this section fit into the process of configuring federated access across your tenant environments, refer to step 2a in the high-level process. |
-
Sign on to the Advanced Identity Cloud admin console of your mutable environment (development or sandbox[4]) as a super administrator[1].
-
Go to Tenant settings.
-
Click Federation.
-
Click + Identity Provider.
-
In the Add Sign On Method modal, select the federation provider to use:
-
Microsoft Azure
-
ADFS
-
OIDC
-
-
Click Next.
-
In the Configure Application modal, click Next.
-
In the Identity Provider Details modal:
-
Complete the following fields:
-
Name: The name of the provider.
-
Application ID: The ID for the application.
-
Application Secret: The client secret for the application.
-
Well-known Endpoint:
-
For Entra ID, this is the URL from the OpenID Connect metadata document field. In the URL, make sure to replace
organizationwith the actual tenant ID for your tenant. -
For AD FS, this is the endpoint from the OpenID Connect section.
-
For OIDC, refer to your IdP vendor’s documentation on locating a client’s well-known endpoint.
When you populate the Well-known Endpoint field with a valid URL, the following fields are automatically populated:
-
Authorization Endpoint: The endpoint for authentication and authorization. The endpoint returns an authorization code to the client.
-
Token Endpoint: The endpoint that receives an authorization code. The endpoint returns an access token.
-
User Info Endpoint: The endpoint that receives an access token. The endpoint returns user attributes.
-
-
(For OIDC only): OAuth Scopes: The scopes the application uses for user authentication. The default scopes are
openid,profile, andemail. -
(For OIDC only): Client Authentication Method: Options are
client_secret_postandclient_secret_basic. The default option isclient_secret_post. -
Button Text: The text for the application button that’s displayed on the tenant’s sign-on page.
-
-
Click Save. By default all users are given the tenant administrator level of access when they access the tenant using your IdP. To give some or all users the super administrator[1] level of access, configure groups in the next step.
-
-
(Optional) Configure group membership to determine administrator access level (super administrator[1] or tenant administrator).
-
Set up groups in your IdP:
-
For Entra ID: Follow the instructions in Use group membership to enable federation in Entra ID.
-
For AD FS: Follow the instructions in Use group membership to enable federation in AD FS.
-
For OIDC: Follow the instructions in Use group membership to enable federation in an OIDC-compliant IdP.
-
-
On the Identity Provider Details page:
-
Select one of the following options:
-
For Entra ID: Enable Use group membership to allow federated sign on to Ping Identity.
-
For AD FS: Enable Use ADFS group membership to allow federated sign on to Ping Identity.
-
For OIDC: Enable Use OIDC group membership to allow federated sign on to Ping Identity.
-
-
Enter the name of the group claim in the Group Claim Name field. For example,
groups.By default, Entra ID sends the IDof the group. You might need to configure it to send thenameof the group. -
To apply an access level to specific IdP groups:
-
To apply the super administrator[1] access level:
-
Locate the Group Identifiers field to the left of
Super Admins. -
Enter one or more group identifiers. For example,
8c578f67-cac4-49eb-8f28-8e4f2c22945e.
-
-
(Optional) To apply the tenant administrator access level:
-
Locate the Group Identifiers field to the left of
Tenant Admins. -
Enter one or more group identifiers. For example,
3623050d-3604-45a2-942e-f6be9ec9f9ed.
-
-
(Optional) To apply the tenant auditor access level:
-
Locate the Group Identifiers field to the left of
Tenant Auditor. -
Enter one or more group identifiers. For example,
eeb11282-cb38-42b9-909f-439cad25550e.
-
-
-
Click Save.
-
-
Configure federation sign-on requirements
After you have enabled federated access to your tenant environments, you can choose how strictly to enforce it. It can be enforced for just tenant administrators or for both tenant administrators and super administrators[1]. These settings are stored in dynamic configuration, so need to be configured per environment.
| To understand how the instructions in this section fit into the process of configuring federated access across your tenant environments, refer to step 5 in the high-level process. |
-
Sign on to the Advanced Identity Cloud admin console as a super administrator[1].
-
Go to Tenant settings, then click the Federation tab.
-
In the Enforcement section, click Edit.
-
On the Edit Tenant Federation Enforcement page, select one of the following items:
-
Optional for All Admins: Allow all administrators to use either their Advanced Identity Cloud credentials or federated access to sign on.
-
Required for All Admins Except Super Admins: Require all administrators that are not super administrators to use federated access to sign on. Super administrators can use their Advanced Identity Cloud credentials or federated access to sign on.
-
Required for All Admins: Require all administrators to use federated access to sign on. If you choose this option, then subsequently need to switch to a lower enforcement level, you must create a support case in the Ping Identity Support Portal.
-
-
Click Update. It can take about 10 minutes for the changes to take effect.
-
On the Change Federation Enforcement? modal:
-
To confirm your changes, click Confirm.
-
To cancel your changes, click Cancel.
-
Deactivate a federation IdP
You can deactivate a federation IdP and reactivate it later. For example, you might want to deactivate a federation IdP if the provider is experiencing technical issues. If you deactivate all federation IdPs for a tenant, tenant administrators can no longer use federation to sign on to the tenant.
You can only deactivate a federation IdP if one of the following is true:
-
Optional for All Adminsis selected as the federation enforcement level (learn more in Configure federation sign-on requirements). -
More than one federation IdP is enabled in the Advanced Identity Cloud tenant.
To deactivate a federation IdP:
-
Sign on to the Advanced Identity Cloud admin console of your development environment as a super administrator[1].
-
Go to Tenant settings, then click Federation.
-
Perform one of the following actions:
-
To deactivate a federation IdP, click the ellipsis icon () to the right of an active federation IdP, then click Deactivate.
-
To activate a federation IdP, click the ellipsis icon () to the right of a deactivated federation IdP, then click Activate.
-
-
Run a series of promotions to move the updated configuration to your UAT[5], staging, and production environments.
Rotate a federation IdP client secret
Most IdPs force you to rotate the client secrets they generate by setting an expiry on the secret. To ensure that federated access continues uninterrupted,you must create and configure a new client secret before the old one expires. If the client secret is stored in an ESV, you can rotate it by creating a new secret version.
For your development, UAT[5], staging, or production environment:
-
In the IdP’s UI:
-
Locate the client configured for the Advanced Identity Cloud environment.
-
Create a new secret and make a note of it:
-
For Azure AD, add a new client secret to the application.
-
For AD FS, reset the client secret for the application group.
-
For OIDC, refer to your IdP vendor’s documentation on creating a new client secret.
-
-
-
In Advanced Identity Cloud admin console:
-
Add a new secret version to the ESV secret using the value of the new federation IdP secret from the previous step. Learn more in Update an ESV referenced by a configuration placeholder.
-