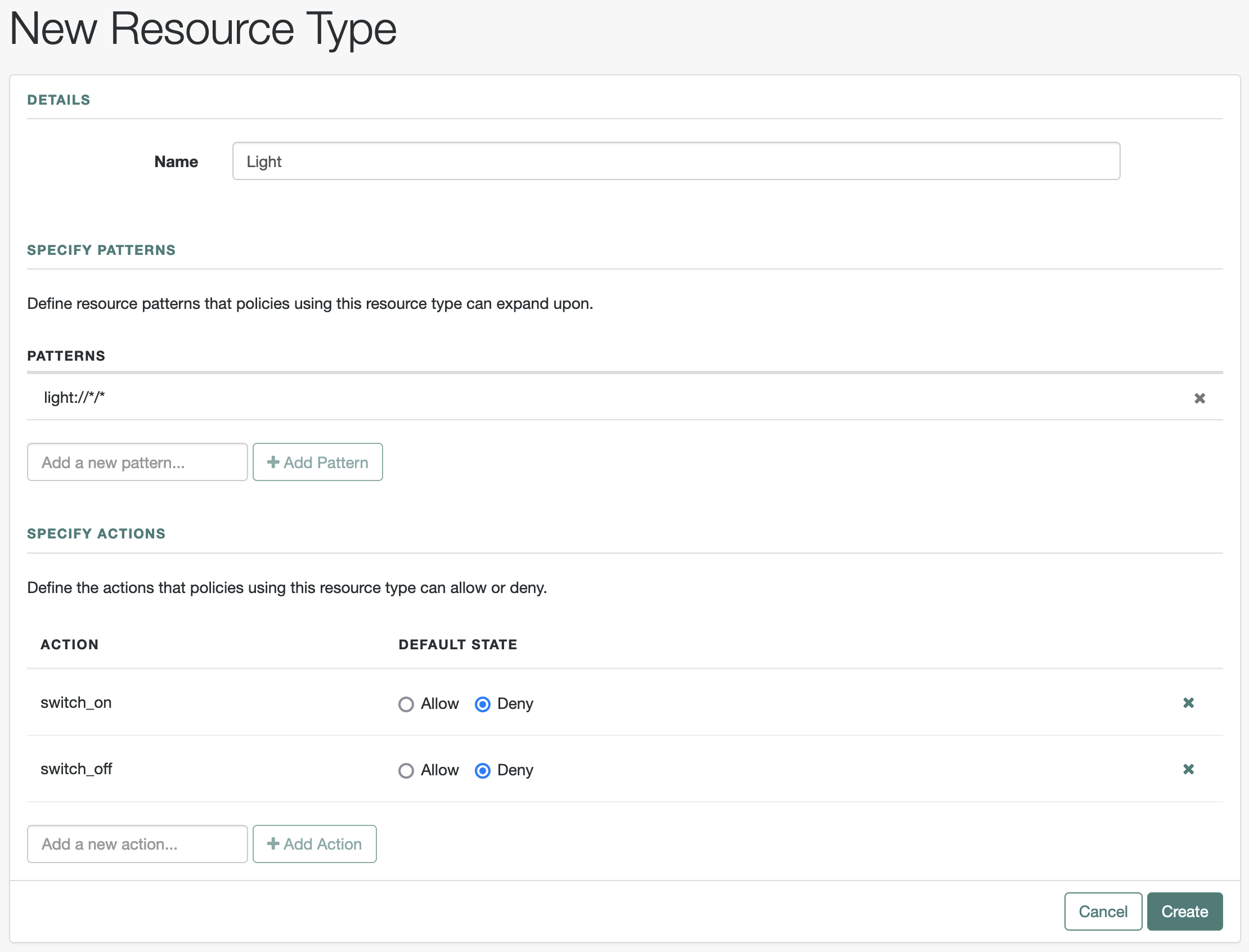
Resource types in the UI
You manage resource types under Native Consoles > Access Management > Realms > Realm Name > Authorization > Resource Types.
| To... | Action |
|---|---|
Create a resource type |
Click New Resource Type. When creating a resource type, specify at least one action and one pattern. |
Modify a resource type |
Click the resource type name or the pencil icon (). |
Delete a resource type |
Click the delete icon () or click the resource type name then the x Delete button. You can’t delete a resource type if any policies or policy sets depend on that resource type. |
Resource type names
Don’t use any of the following characters in policy, policy set, or resource type names:
-
Double quotes (
") -
Plus sign (
+) -
Comma (
,) -
Less than (
<) -
Equals (
=) -
Greater than (
>) -
Backslash (
\) -
Forward slash (
/) -
Semicolon (
;) -
Null (
\u0000)
Resource type patterns
Policies apply to resources that match their patterns.
-
A policy belongs to a policy set.
-
A policy set permits one or more resource types in their policies.
-
A policy can only define patterns that fit the patterns of its resource types.
Wildcards
Resource type patterns can include a mix of literal characters and wildcards, * or -*-.
Wildcards can appear anywhere in a resource type pattern to match resources, such as URLs or OAuth 2.0 scopes.
-
Do not mix
*and-*-in the same pattern. -
Wildcards cannot be escaped.
-
Comparisons are not case-sensitive.
Wildcards in schemes, hosts, and port numbers
When using wildcards for the scheme and authority parts of a URL:
-
The pattern
*://*:*/*matches these URLs:http://www.example.com:80/index.html
https://www.example.com:443/index.html
http://www.example.net:8080/index.html -
Omitting the port number implies the default port number for the scheme:
http://www.example.com/*is the same ashttp://www.example.com:80/*.https://www.example.com/*is the same ashttps://www.example.com:443/*.
Wildcards in paths
Wildcards have these properties in a URL path:
-
The wildcard
*matches multiple path segments.For example,
https://www.example.com/*matcheshttps://www.example.com/,https://www.example.com/index.html, andhttps://www.example.com/company/images/logo.png. -
The wildcard
-*-matches a single path segment.For example,
https://www.example.com/-*-matcheshttps://www.example.com/index.html.It does not match
https://www.example.com/company/resource.htmlorhttps://www.example.com/company/images/logo.png. -
Duplicate slashes (
//) count as a single slash.http://www.example.com//path/andhttp://www.example.com/path//are equivalent. -
A trailing slash counts as a distinct part of the resource to match.
https://www.example.com/pathandhttps://www.example.com/path/are not equivalent.
Wildcards in query strings
Wildcards do not match ?.
Add explicit patterns to match URLs with query strings:
-
When matching URLs protected by a web or Java agent, an asterisk (
*) at the end of a pattern after?matches one or more characters, not zero or more characters.For example,
https://www.example.com/*?*matcheshttps://www.example.com/users?_action=create, nothttps://www.example.com/users?.To match all URLs under
https://www.example.com/, specify three patterns:https://www.example.com/*
https://www.example.com/*?
https://www.example.com/*?* -
When matching resources with a
policies?_action=evaluateREST call, an asterisk (*) at the end of a pattern after?matches zero or more characters.For example,
https://www.example.com/*?*matcheshttps://www.example.com/users?_action=createandhttps://www.example.com/users?.To match all URLs under
http://www.example.com/, specify two patterns:https://www.example.com/*
https://www.example.com/*?* -
Advanced Identity Cloud normalizes query strings before checking whether a policy matches a resource.
To normalize the query string, Advanced Identity Cloud sorts the query string field-value pairs alphabetically by field name. These query strings are equivalent:
?subject=SPBnfm+t5PlP+ISyQhVlplE22A8=&action=get
?action=get&subject=SPBnfm+t5PlP+ISyQhVlplE22A8=
Resource type actions
Advanced Identity Cloud policies use actions to grant or deny access to a resource. A policy can only determine actions defined by its resource types.
Choose a name that summarizes the action the principal aims to perform on the resource. The default state for each action is either Allow or Deny.