Native and Pluggable Authentication Modules (PAM) authentication
API Security Enforcer (ASE) provides two types of authentication:
-
Linux Pluggable Authentication Module (PAM)
-
ASE native authentication (default method)
All actions carried out on ASE require an authenticated user.
The two methods to choose the authentication method include:
-
Configure
auth_methodparameter in thease.conffile. For more information, see ASE Initial Configuration. -
Run a command-line interface (CLI) command (
update_auth_method <method>).
The following diagram shows the transition between authentication modes.
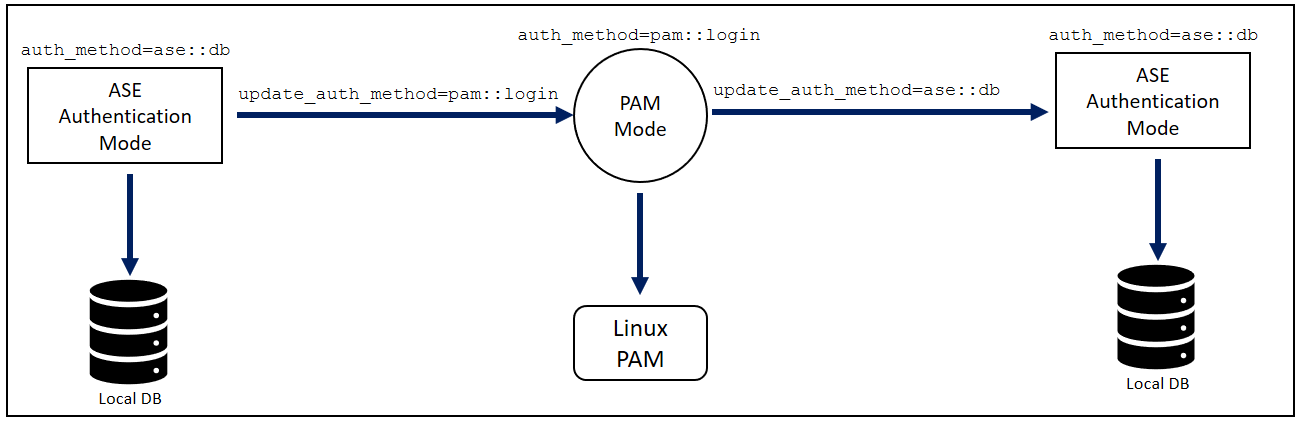
|
The authentication method can be changed during run-time without restarting ASE. |
Configure native and PAM authentication
ASE provides two types of authentication:
-
Linux Pluggable Authentication Module (PAM)
-
ASE native authentication (default method)
All actions carried out on ASE require an authenticated user.
The two methods to choose the authentication method include:
-
Configure
auth_methodparameter inase.conf(see API Security Enforcer) -
Execute a CLI command (
update_auth_method<method>).
The sections below provide more details on configuring the desired method. The following diagram shows the transition between authentication modes. The authentication method can be changed during run-time without restarting ASE.

ASE native authentication
By default, ASE uses native ASE authentication which ships with the system. Each user can execute CLI commands by including the shared “username” and “password” with each command. The system ships with a default username (admin) and password (admin). Always change the default password using the update_password command. For more information on ASE commands, see Appendix A.
To configure ase.conf to support native authentication, use the default configuration values:
auth_method=ase::db
To change the authentication from Native authentication to PAM mode, enter the following command in ASE command line. In the example, login is a PAM script used for authentication.
/opt/pingidentity/ase/bin/cli.sh update_auth_method pam::login -u admin -p password>
To switch from PAM mode authentication back to Native authentication, issue the following CLI command:
/opt/pingidentity/ase/bin/cli.sh update_auth_method ase::db -u <pam_user> -p password>
Here is an example of a CLI command with native authentication (-u,-p) enabled:
/opt/pingidentity/ase/bin/cli.sh add_server -u admin -p password>
Linux PAM authentication
Pluggable Authentication Modules (PAM)-based authentication provides the flexibility to authenticate administrators using existing authentication servers, such as your organization’s LDAP directory. When PAM authentication is active, ASE logs the identity of the user executing each CLI command. This provides a user-specific audit trail of administrative access to the ASE system.
To activate PAM-based authentication, configure auth_method in ase.conf as pam::<service>,where <service> is the script that the PAM module reads to authenticate the users. Service scripts include login, su, ldap, etc. For example, login script allows all system users administrative access to ASE. To support PAM authentication with login script, update auth_method configuration values in ase.conf:
auth_method=pam::login
Here is an example using the CLI to change from Native to PAM authentication with login script:
/opt/pingidentity/ase/bin/cli.sh update_auth_method pam::login -u admin -p password>
|
Make sure that the script name provided for PAM based authentication is the correct one. If a wrong file name is provided, ASE administrators are locked out of ASE. |
To write your own PAM module script, add a custom script (for example ldap) which defines PAM’s behavior for user authentication to the /etc/pam.d directory. To set the authentication method and use the ldap script, enter the following command:
/opt/pingidentity/ase/bin/cli.sh update_auth_method pam::ldap -u admin -p password>
Here is a snippet of a sample script:
root@localhost:/# cat /etc/pam.d/ldap auth sufficient pam_ldap.so # Authenticate with LDAP server. #auth sufficient pam_permit.so # Allow everyone. Pass-through mode. #auth sufficient pam_deny.so # Disallow everyone. Block all access.
In the above example, the PAM module uses the organization’s LDAP server to authenticate users.
Recovering ASE from unavailable pam.dscript
When an invalid script name is entered while changing to PAM authentication, the PAM module defaults to etc/pam.d/others for authentication. This makes ASE inaccessible to administrators. If this happens, copy etc/pam.d/login toetc/pam.d/other. ASE will now use the credentials in etc/pam.d/login to authenticate administrators. After logging back into ASE, change the authentication method to use the correct file name. Copying the contents of etc/pam.d/login to etc/pam.d/other does not need a restart of ASE or the host operating system.