Configuring offline MFA with PingID
Before you begin
Components
-
PingID mobile app 1.8
-
PingFederate 9.1
-
PingID Integration Kit 2.4
|
This use case was developed with the specified product versions. With more recent product versions, the general workflow should apply although specific menu options and screens might differ. |
Do the following:
-
Make sure the components are installed and running.
-
For offline multi-factor authentication (MFA) to work, you must configure it before a service disruption. The device information that is stored in the directory is only populated once the user has authenticated “normally."
About this task
Follow these steps to set up offline MFA to use when the PingID infrastructure is unavailable due to a network outage or similar issue. When a user successfully authenticates while the service is online, PingID returns device information and a public key to PingFederate. PingFederate stores this information in the customer’s directory. In the event of a disruption to the PingID service, PingFederate uses that device information to generate an encrypted QR code.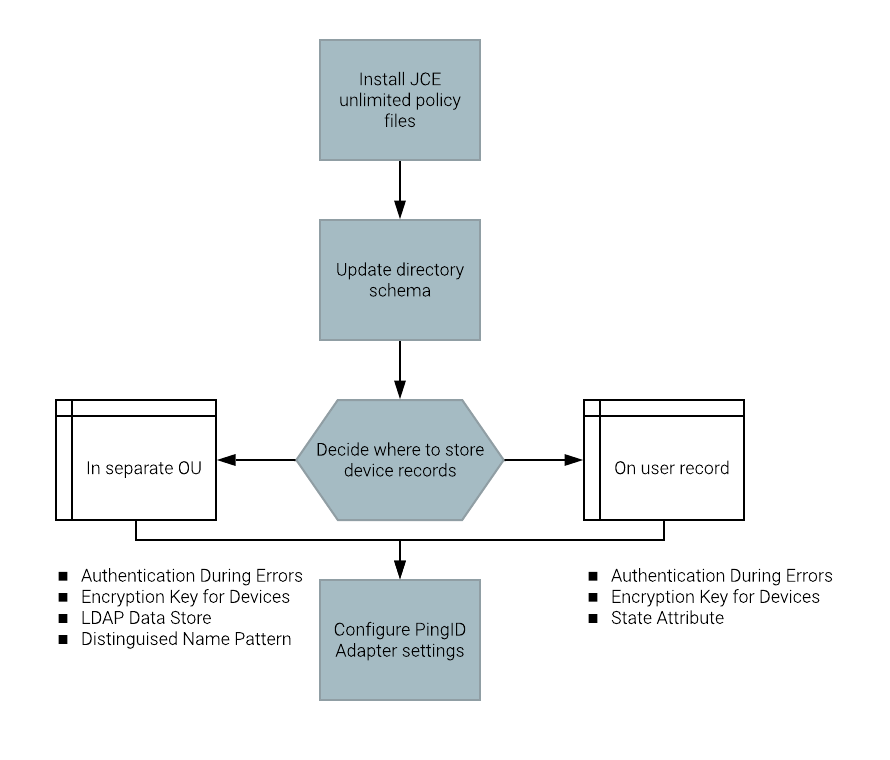
Steps
-
If you do not have the Java Cryptography Extension (JCE) unlimited policy files, download and install them from the Oracle web site at https://www.oracle.com/java/technologies/downloads/archive/#JavaSE.
-
If you use PingDirectory, update the Directory Schema as explained in Configure an LDAP directory for client storage (page 184).
-
Decide where to store device records.
Choose from:
-
Store device records as an attribute on the user record in whatever directory the user records reside.
-
Store device records in a separate organizational unit (OU) that can be in a directory other than where the user records reside.
-
-
Configure PingID Adapter settings as described in Configuring offline MFA (PingID adapter).
-
State Attribute: If you store the device records with the user records, set this value to
Bypass. -
Authentication During Errors: Passive relies on the heartbeat; Enforce will use offline for each attempt.
-
LDAP Data Store: If you store the device records separately from the user records, set the pf-pingid-local-fallback value to the directory in which to store the device records.
-
Encryption Key for Devices: When this key is changed, users need to authenticate online once before an outage occurs.
-
Distinguished Name Pattern: If you store the device records separately from the user records, set the pattern to specify where the device information is stored (for example,
CN={username},OU=PingID-Devices,DC=myDomain,DC=com).
-
-
Test the offline MFA feature.
Choose from:
-
Choose Enforce offline authentication for Authentication During Errors in your PingID Adapter settings.
-
Break the network. For example, set the PingID network to localhost.
-
-
Optional: To configure MFA on Windows while offline, store device information in the Windows registry instead of in Active Directory.
You must configure the Windows behavior during installation.