Configuring access token mapping
Map your policy contract context to the JWT access token manager.
Steps
-
Go go Applications → OAuth → Access Token Mappings.
-
On the Access Token Mappings page in the Context menu, select your policy contract.
-
In the Access Token Manager menu, select your JWT ATM.
-
Click Add Mapping.
-
On the Attribute Sources & User Lookup tab, click Next.
-
On the Contract Fulfillment tab, select a Source and a Value to map into the
admin_role,iss,memberOf, andsubattributes in the Contract list.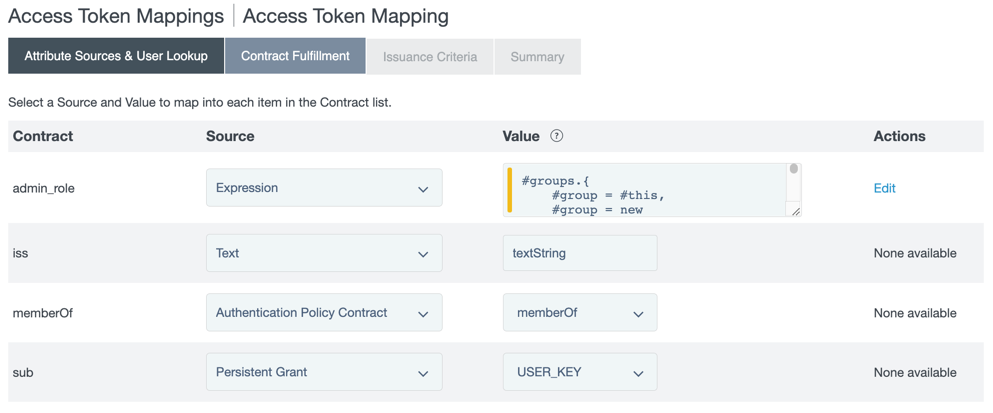
-
For the
admin_roleattribute, select Expression in the Source menu and, in the Value field, enter the following expression:#filter1 = "^pf_admins.*", #filter2 = "^pf_cryptoadmins.*", #filter3 = "^pf_useradmins.*", #filter4 = "^pf_datacollectionadmins.*", #role1 = "admin", #role2 = "cryptoadmin", #role3 = "useradmin", #role4 = "expressionadmin", #role5 = "datacollectionadmin", #outboundattribute = new java.util.ArrayList(), #groups = #this.get("apc.memberOf")!=null?#this.get("apc.memberOf").getValues():{}, #i = 0, #groups.{ #group = #this, #group = new javax.naming.ldap.LdapName(#groups[#i]), #cn = #group.getRdn(#group.size() - 1).getValue().toString(), #cn.matches(#filter1)?#outboundattribute.add(#role1):null, #cn.matches(#filter1)?#outboundattribute.add(#role4):null, #cn.matches(#filter2)?#outboundattribute.add(#role2):null, #cn.matches(#filter3)?#outboundattribute.add(#role3):null, #cn.matches(#filter4)?#outboundattribute.add(#role5):null, #i = #i + 1}, #outboundattribute.size() > 0 ? new org.sourceid.saml20.adapter.attribute.AttributeValue(#outboundattribute):nullThis example OGNL expression gets the
memberOfvalue from the policy contract, looks for group distinguished name (DN) that match the filters, and assigns a role when a filter is matched. In the expression, anyone that is in the Admins group is assigned both the Admin and Expression Admin role, because the Expression Admin role requires the Admin role assignment. Using this expression to map roles allows you to control access with groups from your identity provider’s data source. Match your filter values in the expression to the group names created in your LDAP directory to assign those roles. -
For the
issattribute, select Text in the Source menu, and enter a text string in the Value field.Make a note of the text string. The value entered here is the issuer claim value and should identify the organization as the issuer.
-
For the
memberOfattribute, select Authentication Policy Contract in the Source menu, and memberOf in the Value menu. -
For the
subattribute, select Persistent Grant in the Source menu, and USER_KEY in the Value menu. -
Click Next.
-
-
On the Issuance Criteria tab, click Next.
-
On the Summary tab, review your mappings. Click Save.